Journalists are increasingly using nifty tools like Signal to more easily communicate securely with sources and Tor to anonymously research sensitive subjects. But there's another avenue of techniques and technologies through which reporters can do journalism: tools used by legal hackers.
We're not talking about exploits, password cracking, or anything illegal. Instead, journalists could use programs and tools created primarily for and deployed by hackers to scope out targets, companies, and connections with other items of interest.
Imagine a hacker who is legally authorized to test a company's cyber defenses. Let's say the hacker wants to map out the company's web presence, including websites, email servers, and other info, so they can then decide which bits to probe more closely. The hacker might use something like Maltego, an interface and suite of tools that can quickly search for a website's IP address, pull up extra info from that, and then visualise all those data points and connections.
A journalist can do much the same thing using the same tools. Maybe there is a series of scam sites with no obvious connection, but they actually all share the same Google Analytics code, suggesting a common owner. Or a reporter needs to map out a spyware company and see which other websites it owns.
Maltego is far from the only piece of tech, however, and journalists can use loads of different, smaller tools for more specific tasks. To figure out when a particular Twitter user is online, possibly revealing what timezone they are in, a journalist can scrape a target's tweets and display an overview with a tool called tweets_analyzer. Although not specifically crafted for hackers, specialized Google searches can be used to discover previously hidden PDFs, for example. To more conveniently get hold of these tools in one place, investigators can download a custom operating system like Buscador, which comes preloaded with some of the more common programs.
But to really do these sort of queries at speed, a reporter could use a tool that brings them all together, and automates much of the process.
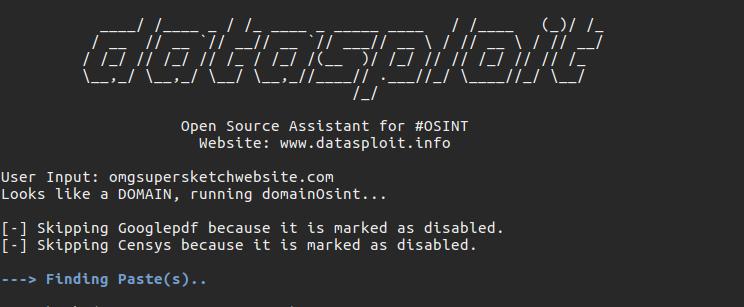
Datasploit is a command-line tool that runs many tasks, such as hunting company emails or querying Wikileaks' databases in quick succession. The tool is modular, meaning a user can pull out and put in different bits of code which conduct different scans as they please. Naturally, it's namesake is Metasploit, the infamous exploit framework that hackers use to test target defenses.
Effective open source intelligence isn't just about discovering new info; it's also about being able to collect and store it en masse. Journalists can use scripts to archive tweets, Facebook profiles, or more, rather than manually screenshotting constantly.
A list of all the useful tools for journalists could just go on and on, but the takeaway is more looking at what techniques others are using, and figuring out how to adapt them to solve your own issues.
Originally published by Vice Motherboard
3 WAYS TO SHOW YOUR SUPPORT
- Log in to post comments